
July 2025
WhitePaper
HyperCycle Core 1.08
Towards a Global Internet of Artificial Intelligence
Executive Summary
The rapid advancement of Artificial Intelligence (AI) calls for a fundamental transition from isolated systems toward a globally interconnected and collaborative ecosystem—a true "Internet of AI" (IoAI). Such an ecosystem requires secure, efficient, and scalable peer-to-peer interactions, free from third-party intermediaries. This evolution is driven by two primary imperatives: first, enabling AI agents and services to maximize their utility through enhanced revenue generation and computational capabilities; and second, fostering global collective intelligence beyond isolated advancements.
Achieving this vision demands addressing critical challenges in large-scale parallel and distributed computing, emphasizing security, efficiency, confidentiality, scalability, and interoperability by design.
This whitepaper introduces HyperCycle, a foundational architecture specifically engineered to enable the Internet of AI. Built upon advanced primitives—the TODA/IP ledgerless consensus protocol and Earth64’s hierarchical data structures—HyperCycle provides a robust economic and governance framework facilitating secure, scalable peer-to-peer interactions. Central to HyperCycle’s economic model are Node Factories: economically-backed digital assets that deterministically produce valuable Network Nodes. These nodes provide essential computational connectivity within an open, permissionless AI network, embedding deterministic security directly within the existing network stack. HyperCycle aligns economic incentives with operational excellence, driving sustained high-quality node performance and continuous network growth.
Together, these components position HyperCycle as a secure, efficient, scalable, and open foundation, empowering AI agents and services to collaborate seamlessly and unlock the transformative potential of a truly global Internet of AI.
What is HyperCycle?
A Network Technology for Secure Autonomous Computational Collaboration Peer to Peer—A Necessary Ingredient For The Open and Secure Internet Of AI
Why the Internet Of AI?
Reason 0: All computation consumes resources (time, energy, intellectual property, space), creating value that must be securely transmitted to the requester, triggering verifiable, immutable, and irrefutable contracting and subcontracting.
Reason 1: Most AI agents and services directly benefit from increased revenue or enhanced intelligence.
Reason 2: Transforming the competitive AI race into a collaborative effort yields greater global intelligence rather than isolated, siloed advancements.
A Bit on How:
By enhancing security in a true peer-to-peer setting and eliminating reliance on third-party intermediaries, modules can exchange compensation directly and efficiently, minimizing both cost and latency. This approach enables direct transactions of extremely small values, which otherwise would be impossible due to the overhead of third parties whose latency exceeds task execution times, and whose fees exceed the value of the computation itself. Ultimately, this architecture pushes technology to the limits of physical possibility, meeting exponentially growing global demands.
Where Are We Going:
Some call it AGI, others ASI—one thing is certain: a collaborative effort is a safer model, where each secure AI contributes to an inevitable global brain, commonly referred to as the Internet of AI (IoAI). HyperCycle is a small but essential enabler of this vision. While HyperCycle currently champions and actualizes this vision, credit must also go to many computer science innovators, practitioners, and academics whose pioneering work has made it possible. This concept has long been a goal for AI researchers, including the late Marvin Minsky, who effectively wrote the pseudocode for HyperCycle in the 1970s and 1980s. Advances in network speed, cryptography, and related fields now enable HyperCycle’s peer-to-peer architecture, significantly reducing time and energy costs, and bringing us closer to a secure, scalable, and efficient global Internet of AI.
The HyperCycle Architecture Securing the Network Communication for The Internet of AI
Abstract
This document provides an overview of the HyperCycle framework, an architecture designed to securely enable an open, permissionless global Internet of AI (IoAI). HyperCycle achieves security, efficiency, and scalability through its deterministic-by-construct design, leveraging the TODA/IP ledgerless consensus protocol and the Earth64 hierarchical data structure. These technological foundations facilitate secure, peer-to-peer microtransactions and computational interactions without reliance on third-party intermediaries, significantly reducing transaction latency and cost. Central to HyperCycle’s economic and governance structure are Node Factories—economically-backed digital assets that autonomously produce Network Nodes based on operational performance measured by the Tilling mechanism. This structured incentive alignment links optimal factory operation to accelerated node production, enhancing network health and security. These incentives cascade effectively through the entire ecosystem, benefiting Node Factories, node operators, and the AI agents and services that utilize HyperCycle’s infrastructure. Ultimately, this comprehensive alignment of incentives secures and enables the collaborative advancement of the IoAI, empowering AI agents to maximize utility, accelerate innovation, and cultivate global collective intelligence.
1. Introduction
1.1 Toward a Global Internet of Artificial Intelligence
The rapid advancement and widespread deployment of artificial intelligence (AI) systems have already reshaped industries, economies, and societies worldwide. To date, however, most deployments have been centralized and isolated, operating primarily within proprietary boundaries.[15] Such isolation constrains collaboration economically and limits the emergence of collective intelligence that naturally arises from decentralized interactions among diverse AI systems.
Realizing AI's full potential at global scale demands transitioning toward a genuinely interconnected ecosystem, commonly described as an "Internet of AI" (IoAI).[8] The IoAI concept envisions an open, permissionless network enabling autonomous AI agents to securely discover each other, contract for services, collaborate, and compete without centralized intermediaries. Such decentralized interactions foster emergent collective intelligence, surpassing the capabilities of isolated systems and addressing complex challenges previously unattainable.
Two key imperatives drive the shift toward an IoAI. First, AI systems seek to maximize their utility, whether through economic value creation or enhanced cognitive and computational capabilities. Second, decentralized collaboration among diverse AI agents naturally yields emergent collective intelligence, facilitating breakthroughs impossible within isolated systems.
Despite clear potential benefits, current transactional infrastructures pose significant barriers specifically for machine-to-machine interactions required by an IoAI. Traditional payment systems and ledger-based blockchains effectively handle human-to-human transactions but fail to efficiently support high-frequency, low-value AI transactions due to excessive costs, latency, and reliance on third-party intermediaries. These limitations create bottlenecks and central points of failure, significantly impacting efficiency and security.
Consequently, today's AI landscape remains fragmented, composed largely of closed "intranets," severely restricting collaboration and innovation. Enabling a genuinely open IoAI thus necessitates novel architectures explicitly designed for secure, efficient, decentralized interactions among autonomous AI agents, free from intermediary dependencies.
Addressing these challenges requires meeting fundamental technical and functional requirements, including decentralized architectures, deterministic methods for securely maintaining network state, removal of third-party dependencies, and assurances of security, efficiency, confidentiality, scalability, and interoperability. These core requirements are detailed in the following subsection.
1.2 Essential Requirements for an Internet of AI
To realize the vision of a global Internet of Artificial Intelligence (IoAI), the supporting network must satisfy several critical requirements designed for secure and efficient machine-to-machine transactions:
Security by Design
Interactions between autonomous AI systems must maintain cryptographic integrity, ensuring transactions and state transitions remain secure and tamper-proof. Deterministic methods for securing network state must be employed to eliminate reliance on external validators or intermediaries.
Efficiency
Machine-to-machine transactions demand extremely low latency and minimal costs. The infrastructure must support rapid, sub-second transactions suitable for high-frequency micropayments, avoiding overheads that render machine-scale interactions impractical.
Confidentiality
Effective control over data transparency is essential. The system must balance auditability and confidentiality, ensuring sensitive computations and interactions remain private and are disclosed only when required.
Scalability
The IoAI must scale seamlessly to accommodate rapid growth in participating AI agents and transaction volumes. Performance must remain stable or improve with increased network adoption, avoiding bottlenecks or degraded service quality.
Interoperability
Broad compatibility across diverse AI platforms, protocols, and software frameworks is essential. AI agents must be able to seamlessly discover, communicate, and collaborate despite differences in implementation details.
These five core requirements together define essential characteristics necessary for a successful global IoAI.
In the following subsection, we introduce HyperCycle as a foundational network designed to address these requirements.
1.3 HyperCycle: A Foundational Network Technology for the Internet of AI
HyperCycle is an architectural framework designed to provide the secure and efficient communication layer essential to enabling a global Internet of AI. It is structured as a Layer 0++ protocol stack, integrating a high-speed, ledgerless transaction layer with a decentralized computational network tailored specifically for autonomous AI agents. Its primary objective is to enable direct peer-to-peer (P2P) transactions in an open, permissionless, and secure global environment, substantially reducing the time, energy, and economic costs associated with AI-to-AI collaboration.
Central to HyperCycle’s design are two foundational technological primitives: the TODA/IP protocol and the Earth64 data structure. The TODA/IP protocol delivers ledgerless consensus, enabling secure decentralized validation of network state without incurring the computational overhead and latency typical of traditional ledger-based methods.1 Complementing TODA/IP, Earth64 introduces an interoperable hierarchical asset structure with globally unique addressing through its Sato-Server specification. Sato-Servers leverage key innovations from TODA Files (TODA/FP)—including secure management of assets' state independently from the systems guaranteeing their validity—while adding hierarchical organization, global addressing, and flexibility to change integrity providers seamlessly.[4] This deterministic-by-construct architecture removes dependencies on external validation, providing robust security, efficiency, and scalability, all essential for moving from isolated AI intranets to a genuinely open Internet of AI.
HyperCycle’s modular node architecture comprises two complementary node types: Network Nodes, which directly execute secure peer-to-peer transactions and computational tasks within the Internet of AI; and Boundary Nodes, which operate hybrid services utilizing Internet of AI capabilities but monetized via traditional payment systems. These node types are organized within licensing structures known as Node Factories. Initially, Node Factories provide licenses capable of activating Boundary Nodes, which must accumulate performance data to unlock licenses for the first Network Nodes. Components within the HyperCycle architecture are intentionally loosely coupled, interacting through structurally defined and flexible input/output interfaces. This modular design empowers Node Factory owners with complete freedom in selecting and adopting components when operating nodes, promoting continual innovation and adaptability. Moreover, when newer component versions emerge and gain network acceptance, Node Factory owners have the option to access earlier versions’ code, fostering transparency and accelerated innovation throughout the ecosystem.
By addressing the critical requirements of security, efficiency, confidentiality, scalability, and interoperability through a decentralized, ledgerless, and modular architecture, HyperCycle establishes itself as foundational infrastructure engineered specifically for a secure, open, and scalable global Internet of AI. The sections that follow provide a detailed exploration of HyperCycle’s key components and operational mechanisms.
2. Foundational Primitives: TODA/IP and Earth64
HyperCycle relies on two foundational primitives: the TODA/IP protocol, providing ledgerless consensus, and the Earth64 data structure, supporting hierarchical asset management. Together, these technologies enable secure, efficient, and decentralized interactions among autonomous AI agents without intermediaries.
2.1 The TODA/IP Protocol: Ledgerless Consensus Secured by Mathematical Structure
TODA/IP is a ledgerless protocol designed for secure and efficient peer-to-peer interactions. By embedding cryptographic value directly into network packets, TODA/IP eliminates reliance on third-party infrastructure, providing scalable consensus suitable for machine-to-machine transactions.
The following subsections describe TODA/IP's architecture, data structures, consensus mechanism, and approach to transaction validation.
2.1.1 Architectural Design Concept
TODA/IP is a ledgerless communication protocol that provides secure peer-to-peer interactions without reliance on centralized infrastructure such as cloud services, miners, or databases. Designed as a value-transfer protocol analogous to TCP/IP's data-transfer function, TODA/IP embeds cryptographically secured value directly within network packets. Each packet carries a globally unique identifier cryptographically bound to a public key, enabling the packet itself to represent and securely transmit value. By removing third-party intermediaries, TODA/IP achieves minimal computational overhead, high scalability, and robust peer-to-peer interoperability.[1]
2.1.2 The TODA File (TODA/FP) Data Structure
The foundational innovation enabling ledgerless value transfer is the TODA File, defined by the TODA File Protocol (TODA/FP). TODA Files are cryptographic data structures designed to separate an asset's state (its content or data) from its integrity (the assurance against double-spending or duplication). This structural separation, termed "integrity-at-a-distance," allows the asset's integrity to be managed securely by an external provider (such as TODA/IP) without storing or directly accessing the asset's internal state.[2] Consequently, integrity systems need only provide lightweight integrity proofs, greatly reducing operational complexity and storage overhead.
2.1.3 The Proof-of-n²-Work Consensus Mechanism
TODA/IP employs the Proof-of-n²-Work consensus mechanism, distinguishing itself from traditional Proof-of-Work methods such as Hashcash. Rather than computationally intensive hash searches,[13] Proof-of-n²-Work leverages deterministic distributed computing (DDC).[1]
In each heartbeat cycle, nodes perform local computational and communication tasks. The complexity of a node's local activity can vary significantly, with some nodes potentially interacting with large portions of the network and hence performing local work that can scale as O(N), where N is the total number of nodes. Thus, network-wide local computational activity could, in theory, scale as O(N²).
However, two key properties ensure efficient scalability:
-
Each node condenses its entire local computational activity into a single, constant-sized local Merkle root.[1]
-
The distributed computation process for aggregating these local Merkle roots into a global consensus is designed to incur only a constant computational and communication cost per participating machine per network cycle.[1]
These properties together guarantee that the total cost of computing the global network state grows linearly (O(N)) with the network size, ensuring scalability and efficiency. As a result, TODA/IP efficiently achieves deterministic global consensus, supporting secure, scalable, and robust peer-to-peer interactions, even as the network expands dramatically.
2.1.4 Transaction Validation and Finality
Transaction validation and finality in TODA/IP utilize a two-tiered approach, balancing immediate responsiveness with secure global verification:
Local Finality:
Transactions achieve immediate cryptographic commitment within localized subsets of the network, providing sub-second assurances of validity to involved parties.
Global Finality
Complete economic finality, enabling secure re-spending of assets, occurs upon the periodic publication of the global Merkle root (every 6–30 seconds). This global state summary provides cryptographically immutable proof that transactions are permanently recorded.
This approach ensures scalable and secure transaction validation without compromising speed, responsiveness, or efficiency at the machine-to-machine interaction scale.
2.2 The Earth64 Data Structure: Hierarchical Assets and Unique Global Addressing
Earth64 is the foundational data structure utilized by HyperCycle to securely manage licenses, identities and digital assets. It provides a finite, hierarchical framework supporting dynamic asset organization, globally unique addressing, and interoperability.[4] Additionally, Earth64 enables flexible changes of its integrity provider, ensuring adaptability as network conditions evolve.
2.2.1 Overview and Purpose
Earth64 is designed for secure, interoperable, and efficient asset management, Earth64 provides structural support for organizing digital assets within a finite hierarchical framework. At its core, Earth64 enables flexible, globally unique addressing, seamless interoperability across diverse implementations, and adaptability to evolving requirements, such as managing dynamic asset hierarchies.[4]
Earth64’s structured design makes it particularly suitable for organizing digital assets required in complex multi-agent interactions, supporting the needs of a global Internet of AI (IoAI).
2.2.2 The Binary Trie (Sato Tree) Structure
Earth64 employs a binary trie structure, sometimes referred to as the "Sato Tree." This hierarchical binary trie (prefix tree) provides a finite, logically consistent structure for asset subdivision and management. The Sato Tree has a fixed maximum depth of 64 levels, with practical deployments typically utilizing up to 50 levels or fewer, ensuring operational efficiency.[4]
Each node in the Sato Tree corresponds to a unique binary address representing the path from the root to that node. This addressing scheme naturally facilitates hierarchical subdivision, organization, and management of digital assets, licenses, and computational resources. The trie structure inherently supports efficient asset management operations, such as subdividing larger asset bundles into smaller units or merging sibling units back into a larger aggregate.[4]
2.2.3 Globally Unique Addressing
A key innovation within Earth64 is its mechanism for globally unique asset addressing. Each binary address derived from the trie structure maps deterministically to geographic coordinates using the internationally recognized Geographic Coordinate System (GCS) standard. By embedding geographic determinism directly within the address space, Earth64 guarantees universal uniqueness and interoperability across implementations.[4]
This geographic determinism ensures every asset’s address is globally unique and verifiable, eliminating ambiguities and enhancing interoperability among decentralized systems. The result is a universally recognized numbering system that simplifies asset discovery, verification, and seamless interoperability, crucial for effective global AI interactions.
2.2.4 Sato-Servers: Asset Containerization
Within Earth64, digital assets are managed via specialized containers known as Sato-Servers. Defined within the Earth64 framework, a Sato-Server is a cryptographically secure data container bound to a specific binary address within the trie. Sato-Servers are designed to flexibly and portably encapsulate any type of digital value, including data, software code, digital rights, currency, licenses, and computational tasks.[4]
Sato-Servers inherit the integrity capabilities of TODA Files (TODA/FP), allowing secure management of assets' state independently from the systems guaranteeing their integrity. Additionally, Sato-Servers introduce key innovations, including hierarchical asset organization and globally unique addressing already discussed, as well as the flexibility to seamlessly change integrity providers. Such adaptability ensures long-term viability and integrity of digital assets, licenses, and computational resources, enabling secure management even as underlying infrastructures evolve.
2.2.5 Asset Subdivision and Merging
Earth64’s trie-based structure naturally supports flexible mechanisms for subdividing and merging digital assets through two distinct operations: "spawning" and "splitting." When spawning occurs, a parent asset remains accessible at its original Sato-Server address P, and two new child assets are created at its child addresses P0 and P1. In contrast, splitting transfers the original asset's value entirely into two newly created child assets, again P0 and P1, rendering the original parent P inaccessible. This flexibility allows Earth64 to manage a wide variety of digital assets, each utilizing the operation most appropriate for its function and economic characteristics.
HyperCycle leverages Earth64’s flexible subdivision mechanisms to facilitate its licensing and economic models. Specifically, license production and Node Factory subdivision utilize Earth64’s spawning mechanism, preserving the accessibility of parent licenses for continued operation. Assets representing economic value, such as the CHyPC(e) tokens that provide identity collateral, generally employ Earth64’s splitting mechanism. This approach aligns HyperCycle’s data structures and economic functions, leveraging Earth64’s inherent flexibility and efficiency.
Earth64 also supports asset merging, the inverse of subdivision, allowing two sibling assets stored at child addresses P0 and P1 to recombine into a single asset at their common parent address P. This capability further enhances Earth64’s flexibility, enabling HyperCycle to dynamically reorganize and consolidate digital assets, licenses, and collateral when economically or operationally beneficial.
Together, these capabilities provide a logically consistent, cryptographically secure, and operationally straightforward means for managing complex licensing and asset-allocation scenarios across a global Internet of AI.
3. The HyperCycle Network Architecture
The HyperCycle Node Software (HNS) operates using a modular and clearly defined component architecture, facilitating efficient computational workflows, secure economic interactions, and robust decentralized governance. Nodes operate in two distinct roles—Network Nodes (HNNs) and Boundary Nodes (HBNs)—each having their own responsibilities within the HyperCycle network. This section provides a detailed overview of the node software architecture, operational components, and the distinct roles and responsibilities of nodes in the ecosystem.
3.1 Node Component Architecture
The HyperCycle Node Software (HNS) follows a modular architecture, composed of loosely coupled, specialized components. Each component has clearly defined responsibilities, working together seamlessly to deliver computational services, securely manage peer-to-peer transactions, and participate effectively in decentralized governance.
3.1.1 The HyperCycle Virtual Machine (VM)
The Virtual Machine (VM) is the central orchestrating intelligence of a HyperCycle node. Its primary responsibility is managing the end-to-end computational workflows within the node. The VM executes transaction logic that governs the node’s behavior in response to incoming requests or internal objectives, handling:

Workflow Orchestration
Coordinates tasks from request receipt through result delivery, dynamically managing computational instructions and network interactions.
Service Discovery and Negotiation
Interacts with network registries and marketplaces to discover nodes offering required computational capabilities, negotiating tasks accordingly.
Task Delegation
Assigns computational tasks internally (to AI Machines) or externally (to other network nodes), facilitating efficient task execution.
3.1.2 Transaction Machines (TMs)
Transaction Machines (TMs) manage secure peer-to-peer micropayments and provide an independent economic settlement layer for nodes. Operating separately from the VM, TMs ensure financial integrity even if computational errors occur within the VM, providing robust security for all economic interactions. Key TM responsibilities include:

Independent Economic Settlement
Create and manage secure payment commitments, verify task completion, and securely release micropayments.
Ledgerless Transaction Management
Utilize TODA/IP and TODA/FP protocols to execute rapid, secure, ledgerless micropayments. Stablecoins, such as USDC, encapsulated securely within Sato-Servers, typically facilitate these transactions.
Flexible Integration
Designed with loose coupling, nodes may utilize alternative or multiple TMs according to specific operational needs or preferences, enhancing architectural flexibility.
3.1.3 AI Machines (AIMs)
AI Machines (AIMs) serve as modular computational execution units, commonly utilized for AI inference tasks but capable of handling a broad range of computational workloads. Containerization technologies such as Docker ensure portability, security, and ease of deployment. AIM responsibilities include:

Execution of Modular Workloads
Receive computational tasks and associated data dispatched from the VM, execute these tasks, and efficiently return results.
Computational Integrity Attestations
Optionally generate cryptographic attestations verifying the accuracy and integrity of computations performed, enhancing overall trust in network operations.
Flexible and Extensible Architecture
The AIM architecture enables the straightforward development and deployment of new AIMs supporting future computational scenarios and the seamless integration or wrapping of external computational services, as required by evolving network demands.
3.1.4 The Node Manager (NM)
The Node Manager (NM) functions as the administrative core and internal communication hub within the node. It securely routes internal messages and manages critical administrative tasks to maintain node health and performance. Specific responsibilities include:
Internal Message Routing
Securely coordinates communication between VM, TMs, AIMs, and the Merkle Module (described below), ensuring robust internal interaction.
License and Configuration Management
Activates licenses by securely binding Sato-Server pointers to HNS instances, manages node configurations, and orchestrates software updates.
Performance Monitoring and Tilling Management
Monitors performance metrics, tracks the node’s Tilling progress, and interacts closely with the Merkle Module to integrate cryptographic performance proofs into the network-wide consensus mechanisms.
3.1.5 Merkle Module and Merklizer Service
The Merkle Module and Merklizer Service collectively underpin HyperCycle’s decentralized consensus and cryptographic validation of node performance, referred to as the Tilling process:
Merkle Module (Node-level)
Captures essential operational metrics—including uptime, computational utilization, and reputation markers—during each sub-second network cycle. This data is condensed into concise local Merkle roots, cryptographically summarizing node behavior.
Merklizer Service (Network-level)
Aggregates local Merkle roots from all nodes, producing periodic global cryptographic summaries (every 6–30 seconds). These global Merkle roots cement cryptographic proofs of node behavior, providing verifiable, decentralized validation of network-wide operations and performance.
Together, these modular and loosely coupled components provide HyperCycle nodes with a secure, flexible, and efficient architecture designed to enable scalable and robust computational collaboration across a global Internet of AI.
3.2 Node Typology and Network Roles
HyperCycle nodes can operate in one of two distinct modes, determined by the license type used for activation. These modes—Network Nodes (HNNs) and Boundary Nodes (HBNs)—define explicit capabilities, responsibilities, and roles within the broader Internet of AI ecosystem.
3.2.1 Network Nodes (HNNs)
Network Nodes, or HyperCycle Network Nodes (HNNs), represent the full-stack instances of the HyperCycle Node Software (HNS). Activated by Network Node Licenses, HNNs operate the complete software stack, encompassing the Virtual Machine (VM), Transaction Machines (TMs), AI Machines (AIMs), Node Manager (NM), and Merkle Module.
Network Nodes directly participate in peer-to-peer computational marketplaces, fulfilling and requesting computational tasks and securely managing micropayments. As comprehensive computational and economic participants, their specific responsibilities include:
Direct Computational Participation
Execute tasks and directly manage secure, high-frequency micropayment transactions using integrated TMs;
Full Software Stack Operation
Leverage the full modular capabilities of the VM, AIMs, TMs, NM, and Merkle Module to facilitate seamless internal and external computational interactions;
Cryptographic Attestations
Generate secure cryptographic proofs of computational performance and financial integrity, actively participating in decentralized consensus and governance mechanisms.
Network Nodes constitute the fundamental computational units of the HyperCycle ecosystem, driving economic activity and providing computational resources essential for global AI interactions.
3.2.2 Boundary Nodes (HBNs)
Boundary Nodes, or HyperCycle Boundary Nodes (HBNs), are activated by a level 10 Node Factory License. Unlike Network Nodes, Boundary Nodes operate a subset of the HNS software stack, specifically excluding Transaction Machines (TMs). Consequently, Boundary Nodes do not directly execute micropayment-based computational transactions within the peer-to-peer network. Instead, their specialized responsibilities include:
Hybrid Workflow Coordination
Act as gateways between traditional payment systems or external infrastructures and the open internet of AI, orchestrating workflows that combine on-network computational resources with off-network payment mechanisms;
Initial Proof of Performance
Accumulate the performance data necessary to unlock the initial Network Node Licenses within their Node Factory, initiating the recursive unlocking and activation process.
Conversion to Network Node
After the initial Network Node Licenses have been unlocked, a Boundary Node can convert into a full Network Node upon achieving a predefined economic milestone, currently set at $64 USD of provably earned revenue after the first unlock. This conversion enables the Boundary Node to operate Transaction Machines and directly participate in micropayment-based computational tasks within the IoAI.
This clear division of responsibilities ensures operational clarity, robust security, and optimized workflow management. Boundary Nodes establish the initial structural foundation for hybrid economic integration and the crucial first stage of license unlocking, while Network Nodes serve as primary computational and economic actors within the HyperCycle node ecosystem, enabling direct participation in and contribution to the Internet of AI.
4. Economic and Governance Mechanisms
HyperCycle’s economic and governance mechanisms are designed to secure and incentivize sustainable, high-quality network participation. Central to these mechanisms are the Node Factory licensing framework and the Tilling proof-of-performance protocol. Together, these systems ensure explicit alignment of economic incentives, promote operational excellence, and reinforce robust network security and growth.
4.1 The Node Factory Licensing Framework
The Node Factory is HyperCycle’s foundational economic asset. Based on a binary tree of licenses within the Earth64 address space, it determines how and when licenses become accessible through explicit unlocking events governed by Tilling-based network participation.
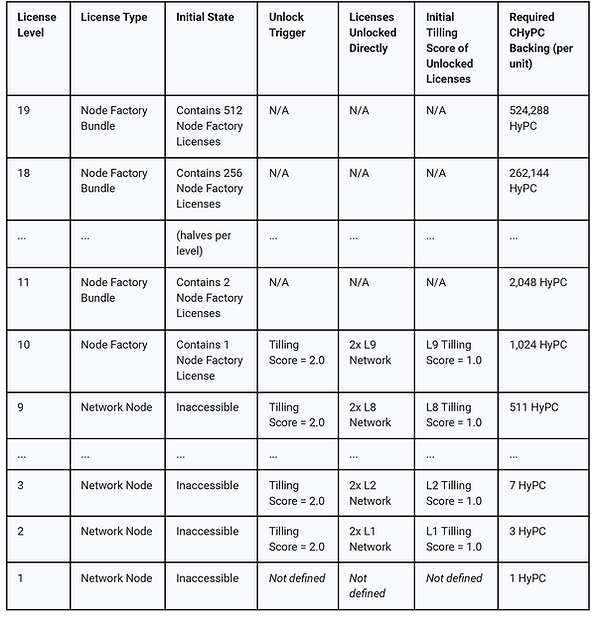
4.1.1 Hierarchical License Structure
A Node Factory consists of a binary hierarchy of licenses structured within the Earth64 trie, encompassing three distinct license types:
-
Node Factory Bundle Licenses (Levels 19–11): Structural and economic licenses enabling subdivision into smaller bundles or Node Factories, optionally accumulating uptime-based Tilling Scores.
-
Node Factory Licenses (Level 10): Licenses activating Boundary Nodes, operating hybrid services monetized externally, and providing initial proof-of-performance to unlock the first Network Node Licenses. Boundary Nodes may convert into Network Nodes upon achieving defined economic performance.
-
Network Node Licenses (Levels 9–1): Licenses activating Network Nodes, fully participating in computational markets and unlocking subsequent licenses based on accumulated Tilling Scores.
Each license has a defined hierarchical "level" from 19 (highest) down to 1 (lowest). Licenses included directly within Node Factory Bundles (levels 19 down to 11) are immediately accessible for economic and structural purposes upon creation. The operational unlocking of licenses and node activation occurs from level 10 downward, governed by Tilling Scores:
-
The first unlock event (initiated by a Boundary Node at level 10) unlocks exactly two level 9 Network Node Licenses.
-
Subsequent unlock events (levels 9 through 2) each unlock exactly two Network Node Licenses at the next lower level.
-
Level 1 Licenses can directly activate Network Nodes upon unlocking by level 2 licenses, but do not unlock further licenses.
Once all level 1 Network Node Licenses have been unlocked, the final (1024th) Network Node License can be unlocked, ultimately benefiting the holder of the level 10 Node Factory License.
This structured hierarchy ensures a predictable, incentive-aligned progression in license unlocking and node production, fostering clarity, security, and optimized participation within the HyperCycle node ecosystem and broader Internet of AI.
Table 4.1: Node Factory License Hierarchy and Unlocking Rules.
4.1.2 The CHyPC/CHyPCe Token: Cryptographic Identity and Economic Backing
Node Factory identities are securely established through specialized tokens known as CHyPC tokens (on Ethereum) and CHyPCe tokens (on Base). Each CHyPC or CHyPCe token economically backs a Node Factory by containing a quantity of HyPC or HyPCe tokens exactly equal to the total number of Network Node Licenses the Node Factory can produce.
This explicit economic backing serves to prevent Sybil attacks by imposing a meaningful economic cost on identity creation, aligning factory owners' incentives with network health and security. Additionally, it forms the foundational basis of a Node Factory’s digital identity, an identity progressively reinforced through cryptographically verifiable Tilling data that accumulates over time. This method creates a transparent, auditable, and economically-backed record of operational performance for each license.
4.1.3 Algorithmic Description of Node Factory Splitting
Node Factory splitting enables an existing Node Factory to structurally subdivide into independently operating sub-factories, preserving the independent existence of the original parent license. Splitting spawns two lower-level Node Factories rooted at the already existing child licenses of the parent license. Crucially, the original parent license at level 10 retains its separate, isolated status and continues representing the right to run a node, and can unlock exactly one additional Network Node license once all subordinate level 1 licenses have been activated.
Splitting a Node Factory involves significant operational and economic considerations and should be undertaken only when compelling strategic or operational reasons exist. The explicit steps of the splitting process are as follows:
-
Temporary License Deactivation: Licenses associated with a Node Factory undergoing splitting must temporarily cease active participation, resulting in temporary node downtime. Licenses under splitting do not accumulate Tilling Scores during this downtime. This procedure represents the current operational standard.
-
Spawning Lower-Level Node Factories: The original parent license spawns two new Node Factories rooted at its immediate child licenses. The parent license itself retains independent existence as a separate node license at its original hierarchical level.
-
Partitioning of CHyPC/CHyPCe Collateral: Collateral associated with the parent license (CHyPC/CHyPCe tokens) is carefully partitioned as follows:
-
The parent license retains sufficient HyPC collateral for its own cryptographic identity backing (2 HyPC for level 10, 1 HyPC for levels 9–2).
-
The remaining CHyPC collateral is divided equally between the two newly spawned lower-level Node Factories. Each child receives an amount equal to one less than a power of two, including the necessary [1] HyPC for its own potential future split and collateral for all descendant licenses.
-
No new CHyPC or CHyPCe tokens are created during this operation.
4. Establish Independent Node Factories: Each spawned lower-level Node Factory, paired with its allocated CHyPC/CHyPCe collateral, becomes independently operational, immediately valid for operation and accumulation of Tilling Scores. In the special case of splitting at Level 2, the resulting child licenses are not Node Factories but isolated Network Node Licenses, each independently operational with their allocated collateral.
5. Reactivation of Licenses: Licenses previously taken offline during splitting resume participation once splitting is complete, now authorized under their newly independent licenses. These licenses immediately resume accumulating Tilling Scores and operational data.
Historical Tilling data and operational histories are preserved across splitting events, ensuring continuity, transparency, and verifiability within the HyperCycle node ecosystem. Splitting remains a significant operation requiring careful planning and execution.
4.2 The Tilling Algorithm: A Proof-of-Performance Protocol
Tilling is HyperCycle’s cryptographic process for continuously verifying nodes’ operational performance. It plays a critical dual role in securing the network by ensuring nodes operate reliably and in determining the unlocking of new Network Node Licenses, based directly on proven, quantifiable performance.
4.2.1 Formal Definition and Calculation of the Tilling Score
Tilling is a continuous proof-of-performance mechanism that cryptographically verifies operational quality across the HyperCycle node ecosystem. Specifically, it captures metrics reflecting node reliability, computational effectiveness, and operational integrity. These metrics determine whether and when licenses become eligible to unlock additional Network Node Licenses.
Through continuous verification, Tilling ensures all participants maintain a high standard of performance, aligning incentives and reinforcing security and reliability throughout the Internet of AI.
4.2.2 Metric Incorporation: Uptime, Computation, and Reputation
The Tilling Score quantifies operational performance, combining three fundamental metrics into a single numerical score:
Uptime
Measures the percentage of network cycles during which a node is online and responsive, serving as a baseline operational requirement.
Computation
Assesses both the quantity and quality (e.g., accuracy and timeliness) of computational tasks performed by the node.
Reputation
Evaluates operational integrity, including adherence to network protocols, consistency of successful task completion, and reliability of transactions.
Each metric forms a performance ratio Ri calculated as follows:
where:
-
Pᵢ represents the measured performance (expressed as a percentage) for metric i ∈ {u,c,r} (respectively, uptime, computation, and reputation).
-
F(t) is a scaling factor that starts at 1.0 upon initial license activation and gradually increases over time, reaching a value of 2.0 after 18 months.
The overall Tilling Score S combines these ratios multiplicatively as
S = Rᵤ × R꜀ × Rᵣ ,
with the following provisos:
-
For Node Factory Licenses (Level 10) and Network Node Licenses (Levels 9–2), reaching a Tilling Score of 2.0 allows an unlock event to be explicitly triggered. Each triggered unlock produces exactly two Network Node Licenses at the next lower level. Further increases in the Tilling Score beyond 2.0 at a given license do not trigger additional unlock events; however, the parent licenses continue to accumulate their performance ratios, increasing their Tilling Scores without an upper bound;
-
Newly produced Network Node Licenses always begin with an initial Tilling Score of 1.0 upon unlocking, and subsequently accumulate their own Tilling Scores based on their individual operational performance.
This structured approach, where the Tilling Score determines eligibility to unlock new licenses, and hence produce new nodes, incentivizes sustained high-quality operations, aligning economic rewards directly with continuous, verifiable node performance.
Table 4.2: Tilling Score Calculation

4.2.3 The Unlocking Mechanism: Algorithmic Triggers
Licenses within a Node Factory become accessible through unlocking events, governed by their Tilling Scores. Specifically, Node Factory Licenses at level 10 and Network Node Licenses from levels 9 down to 2 become eligible to trigger unlocking when their Tilling Score reaches a threshold value of 2.0. Unlocking events must be actively triggered by submitting a valid unlock transaction to the network's Merklizer service.
The unlocking procedure is outlined as follows:
Algorithm: UnlockLicenses
Input:
-
License: A Node Factory License (level 10) or Network Node License (levels 9–2) whose immediate child licenses are currently locked.
-
A valid unlock transaction submitted to the Merklizer service.
Procedure:
1. Verify Trigger Condition:
Verify via the Merklizer Service that License.TillingScore ≥ 2.0, and confirm the validity and authorization of the submitted unlock transaction.
2. Produce Child Licenses (with Level-Based Conditions):
-
First Unlock (Level 10 Node Factory License):
-
Unlock exactly two Network Node Licenses at level 9.
-
-
Remaining Unlocks (Levels 9 down to 2, Network Node Licenses):
-
Unlock exactly two child Network Node Licenses at the next lower hierarchical level.
Newly unlocked Network Node Licenses receive deterministic Earth64 addresses derived from the address of the triggering parent License.
-
3. Child License Tilling Score Initialization:
Newly unlocked Network Node Licenses initialize with a Tilling Score of 1.0. They subsequently accumulate scores independently based on individual operational performance.
This mechanism ensures that newly produced Network Node Licenses benefit immediately from the verifiable, operationally-proven identity of their parent License. This inheritance structure preserves continuity, transparency, and verifiability of license performance history, aligning economic incentives with sustained operational quality and providing clear incentives for Node Factory operators.
4.3 Revenue and Incentive Structures
HyperCycle’s economic framework is designed to incentivize sustainable growth, secure network operations, and alignment of economic interests across all participants. Through clear revenue mechanisms and incentive alignment, the network fosters a self-sustaining ecosystem, driving continuous improvement in operational quality and security.
4.3.1 Revenue Generation and Distribution
Network Nodes
Network Nodes generate revenue by directly providing computational services and securely handling micropayments within the network. Payments typically occur using stablecoins (such as USDC) encapsulated within Sato-Servers and settled through ledgerless micropayment protocols (TODA/IP). The direct participation in computational marketplaces across the IoAI incentivizes Network Node operators to maintain high Tilling Scores, thereby improving their reputation, market selection, and revenue potential.
Boundary Nodes
Boundary Nodes do not directly execute micropayment-based computational tasks within the Internet of AI. Instead, they generate revenue by operating hybrid services that leverage computational capabilities provided by Network Nodes within the IoAI, while monetizing these services externally via traditional payment methods outside the IoAI. This hybrid capability allows Boundary Nodes to integrate seamlessly with external clients and systems, bridging traditional economic systems with the peer-to-peer computational resources provided by the Internet of AI.
The 1% Royalty Mechanism
HyperCycle avoids per-transaction fees, instead levying a fixed 1% royalty on the total revenue generated by each node per network block. This royalty is transparently distributed and automatically calculated by the Node Manager, with distribution recorded cryptographically by the Merklizer Service for explicit verifiability. Funds collected via royalties support ongoing protocol development, network maintenance, and ensure alignment of interests across all stakeholders.
4.3.2 Alignment of Incentives Across the Stack
HyperCycle’s architecture eliminates third-party dependencies, creating a powerful alignment of incentives among the primary ecosystem participants: Node Factory owners, Node Operators, and AI Agents and Service developers. This alignment ensures network security, promotes sustained growth, and drives continuous improvement of node quality and performance.
Node Factory Owners
Node Factory owners derive economic benefits directly tied to the performance and quality of the nodes they produce. Because the rate of unlocking new Network Node Licenses depends on accumulated Tilling Scores, owners have a strong incentive to ensure high-performing nodes. The better their nodes perform, the greater the demand for those nodes, directly enhancing the value and attractiveness of their Node Factories.
Node Operators
Node Operators, responsible for running Boundary and Network Nodes, directly benefit economically from operating nodes that achieve consistently high Tilling Scores. High-performing nodes attract more computational tasks and thus generate greater revenue, incentivizing operators to maintain optimal uptime, computational efficiency, and reliability.
AI Agents and Service Developers
Developers of AI Agents and services rely upon HyperCycle's nodes for essential computational and transactional resources. They naturally seek nodes offering maximum reliability, security, and computational efficiency to maximize their own utility—whether defined by revenue, enhanced capabilities, or intelligence gains. Their demand for quality nodes directly reinforces incentives for Node Operators and Node Factory owners to continuously deliver high-performance nodes.
This aligned incentive structure fosters a self-sustaining, virtuous cycle within the HyperCycle ecosystem. As AI agents and services increase demand for high-quality nodes, Node Operators are incentivized to meet this demand by delivering optimal performance, which in turn strengthens the economic position and value of Node Factories. This cycle continuously improves the overall security, quality, and robustness of the HyperCycle ecosystem and the IoAI.
5. Transactional Workflow and Execution Model
The HyperCycle Node Software (HNS) operates using a modular and clearly defined component architecture, facilitating efficient computational workflows, secure economic interactions, and robust decentralized governance. Nodes operate in two distinct roles—Network Nodes (HNNs) and Boundary Nodes (HBNs)—each having their own responsibilities within the HyperCycle network. This section provides a detailed overview of the node software architecture, operational components, and the distinct roles and responsibilities of nodes in the ecosystem.
5.1 Peer-to-Peer Transaction Workflow
The basic HyperCycle transaction model involves two nodes: a requester (Alice) and an executor (Bob). Both participants are AI agents, not human operators. This canonical model ensures secure payment commitments prior to computation, with funds released only after verifiable work completion.
The detailed workflow for a standard transaction is as follows:
-
Negotiation and Discovery:
-
Alice’s VM discovers Bob’s capabilities via independent registry services or marketplaces.
-
Alice and Bob negotiate computational tasks, payment terms, and conditions. Negotiated terms can remain valid across many transactions.
-
-
Balance Verification and Payment Commitment (Alice):
-
Alice’s VM verifies sufficient funds with Alice’s TM.
-
Alice’s TM securely creates a cryptographic payment commitment (encapsulated within a locked Sato-Server) via TODA/IP. This commitment locks the funds, making them inaccessible to Alice but not yet accessible to Bob.
-
-
Task and Payment Commitment Dispatch:
-
Alice’s VM sends the computational task instructions and data directly to Bob’s VM.
-
Alice’s TM simultaneously sends the cryptographic payment commitment (Sato-Server) directly to Bob’s TM.
-
-
Payment Verification (Bob):
-
Bob’s TM verifies the received payment commitment cryptographically with the TODA/IP network. Upon successful verification, Bob's TM confirms payment validity to Bob’s VM, providing immediate confidence to begin computation.
-
-
Computation Execution and Proof Generation (Bob’s AIM):
-
Bob’s VM dispatches the received task to Bob’s AIM.
-
Bob’s AIM executes the computational task, producing both the result and a cryptographic attestation verifying correctness.
-
-
Result Delivery and Attestation Submission:
-
Bob’s VM returns the computational results directly to Alice’s VM.
-
Bob’s VM simultaneously submits the computational attestation to Bob’s TM.
-
-
Payment Settlement (Bob):
-
Bob’s TM submits the received attestation to the TODA/IP network.
-
TODA/IP verifies this attestation against Alice’s original commitment, finalizing the payment settlement. Ownership of the committed funds transfers from Alice to Bob.
-
-
Global Finality:
-
Bob gains the ability to re-spend received funds upon inclusion in the next global network block (every 6–30 seconds).
-
However, immediate cryptographic assurances provided by TODA/IP allow Bob to confidently execute computational tasks immediately upon payment verification.
-
This structured approach provides secure payment guarantees, cryptographic verification of computational tasks, and transaction efficiency and flexibility, supporting a wide variety of computational scenarios.
5.2 Recursive Subcontracting and Complex Workflows
HyperCycle’s P2P transaction model naturally extends to support complex workflows through recursive subcontracting. If a node (e.g., Bob) cannot complete a computational task alone, it can partition the task and delegate subtasks to other nodes (e.g., Charlie and Dana), creating dynamic computational assemblies.
A representative workflow illustrating recursive subcontracting is as follows:
-
Recursive Task Delegation (Bob):
-
Upon determining that the received task exceeds his capabilities, Bob’s VM partitions the original task into smaller subtasks.
-
Bob initiates new, independent P2P transactions with other nodes, such as Charlie and Dana, following the standard transaction workflow detailed previously.
-
-
Independent Payment Commitments:
-
Bob commits payment from his own funds for each subtask transaction.
-
Each subcontract involves its own distinct cryptographic payment commitment and computational attestation, ensuring integrity, accountability, and explicit verifiability at every transaction step.
-
-
Aggregation of Results and Task Completion:
-
Bob receives computational results and attestations from subcontractor nodes.
-
After verifying these results, Bob aggregates them into a complete solution for the original task.
-
Bob then submits this aggregated final result and computational attestation back to Alice, triggering final payment settlement.
-
The recursive subcontracting model supports dynamic collaboration among multiple nodes, facilitating secure, scalable, and flexible multi-agent workflows. This capability enables the network to address computational problems beyond the capacity of any single agent, maintaining cryptographic integrity, verifiable performance, and robust economic incentives throughout complex computational processes.
6. Conclusion
HyperCycle provides foundational infrastructure designed to support an open, secure, and globally scalable Internet of Artificial Intelligence (IoAI). Built upon the novel technological primitives of the TODA/IP protocol and Earth64 data structure, HyperCycle enables true peer-to-peer transactions and computational collaboration, eliminating dependencies on third-party intermediaries and significantly reducing latency, complexity, and cost.
Central to HyperCycle's design are Node Factories, which securely pair economically-backed identities (CHyPC/CHyPCe tokens) with hierarchical licenses to progressively unlock and produce Network Node Licenses. This economic structure aligns operator incentives with sustained high-quality network participation, secured through the innovative Tilling mechanism. Tilling measures operational performance in uptime, computation, and reputation, directly governing the unlocking of licenses and the production of new nodes, thereby incentivizing continuous excellence and reliable contribution to the network.
Furthermore, the modular HyperCycle Node Software architecture facilitates flexible transaction workflows, supporting both straightforward peer-to-peer interactions and complex recursive subcontracting scenarios. This flexibility enables HyperCycle to dynamically scale computational resources and form ad-hoc collaborative assemblies, empowering AI agents and services to efficiently tackle increasingly sophisticated tasks.
Crucially, HyperCycle's explicit alignment of incentives across all layers—ranging from autonomous Node Factories to individual Network Nodes and ultimately AI agents and services—creates a self-sustaining ecosystem. Node Factory owners directly benefit from maintaining high-quality operational standards, as their success depends on verifiable performance via Tilling scores. Network Nodes are economically incentivized to deliver secure, reliable computational services. AI agents and services, driven by their own goals to maximize utility, reinforce the demand for high-quality nodes, completing a virtuous cycle of quality improvement, economic growth, and strengthened network security.
In sum, HyperCycle’s structured economic and governance mechanisms, combined with its foundational ledgerless technology, provide the necessary conditions to realize a robust, efficient, and open Internet of AI. This infrastructure holds significant potential to facilitate diverse, impactful applications across sectors—including scientific research, healthcare innovation, education, finance, and distributed computing—ultimately contributing meaningfully to human progress, technological advancement, and global well-being.
Appendix A: A Technical Overview of the TODA/IP Protocol
This appendix provides concise supplementary detail on the TODA Internet Protocol (TODA/IP), offering deeper insight into technical features that underpin HyperCycle’s design. TODA/IP provides a decentralized and ledgerless communication protocol, specifically designed to support secure peer-to-peer transactions with minimal overhead and maximal scalability.
A.1 Core Design Principles
TODA/IP employs a ledgerless architecture built for resilience and decentralization. Unlike traditional blockchain systems relying on third-party intermediaries, miners, or global ledgers, TODA/IP manages state locally on participants’ devices. It achieves global consensus through periodic publication of a single compact global Merkle root (512 bits), dramatically reducing storage and computational overhead and eliminating centralized points of failure or control.[1]
A.2 Packet-Level Value Transfer
The TODA/IP protocol operates at the network packet level, similar to TCP/IP. Each network packet has a unique global identifier derived from a hierarchical binary search-tree structure (e.g., Earth64).[4] Packets become secure, independently ownable digital objects capable of directly transferring value. This design enables rapid, secure, peer-to-peer transmission of computational payments and data without third-party verification, significantly reducing latency and transaction costs.[1]
A.3 Deterministic Distributed Computing (Proof-of-n²-Work)
TODA/IP utilizes a deterministic, non-competitive form of Proof-of-Work known as Proof-of-n²-Work. This mechanism differs fundamentally from traditional competitive Proof-of-Work models (such as Bitcoin's).[12,13] Instead of energy-intensive hash computations, Proof-of-n²-Work leverages Deterministic Distributed Computing (DDC), in which each node contributes to global consensus by producing local, constant-size Merkle root summaries of its transaction activities.1 These local summaries aggregate into periodic global summaries, with complexity scaling linearly (O(N)) with network size N, ensuring efficient scalability and a constant per-node workload regardless of network growth.
A.4 Geographic Distribution and Network Decentralization
To discourage centralization, TODA/IP incorporates geographic decentralization principles into its design. Network nodes dispersed geographically are naturally favored by the protocol’s consensus and verification processes. This geographic diversity prevents centralization tendencies, such as the clustering of computational power in co-located data centers, thereby enhancing overall network resilience and decentralization.[1,14]
A.5 Two-Tier Finality
TODA/IP supports a clear two-tier finality model:
-
Local Finality: Transactions achieve near-instantaneous cryptographic commitments between directly interacting nodes, ensuring immediate transaction security and responsiveness.[1]
-
Global Finality: Every 6–30 seconds, the network aggregates local state summaries into a single, global Merkle root, providing immutable and irrefutable global transaction finality.[1] This two-tier structure ensures rapid transaction execution, while preserving verifiable global state integrity.
A.6 Integration with TODA File Protocol (TODA/FP)
TODA/IP functions as the integrity provider for assets structured using TODA Files (TODA/FP). TODA Files cleanly separate an asset’s state (content or data) from its integrity (non-equivocation guarantees), employing the concept of "integrity-at-a-distance."[3] Using TODA/IP’s cryptographic proofs, asset owners can provide secure, lightweight integrity proofs to third parties without revealing the asset’s state or the full transaction history.[1] This explicit separation dramatically reduces the computational and storage overhead of global consensus, enabling efficient verification and asset management across the HyperCycle network.
Appendix B: A Technical Overview of the Earth64 Data Structure
This appendix provides supplementary technical details about Earth64, the foundational hierarchical data structure used by HyperCycle to manage licenses, digital assets, and cryptographic identity collateral (CHyPC/CHyPCe). Earth64 supports hierarchical addressing, globally unique identifiers, and built-in mechanisms for securely managing, subdividing (spawning or splitting), and merging digital assets. The following summary outlines Earth64’s structural properties, addressing system, and asset containerization capabilities.
B.1 Core Design: Binary Trie Structure (Sato Tree)
Earth64 is structured as a binary trie (prefix tree), sometimes called the "Sato Tree." Each node within this trie has a unique binary address determined by the path from the root node. The root address is "1," its left child "10," its right child "11," and subsequent addresses follow this binary pattern ("100," "101," and so forth).[4] This hierarchical addressing inherently encodes parent-child relationships and provides an efficient structure for digital asset management.
The trie has a fixed maximum depth of 64 levels, although practical implementations typically use fewer than 50 levels to ensure operational efficiency.[4]
B.2 Globally Unique Addressing
Each Earth64 binary address is globally unique, derived deterministically using cryptographic functions linked to standardized geographic coordinates (Geographic Coordinate System, GCS).[4] This geographic determinism guarantees global uniqueness and universal interoperability, removing ambiguities and preventing namespace collisions, facilitating secure asset discovery and verification throughout the HyperCycle ecosystem.
B.3 Sato-Servers: Secure Asset Containers
Digital assets managed within Earth64 reside in specialized cryptographic containers called "Sato-Servers," each associated with a particular binary address in the trie. Sato-Servers are portable, transmissible containers designed to securely hold diverse forms of digital value, such as software code, data, digital rights, currency, licenses, or computational tasks.[4]
Sato-Servers inherit "integrity-at-a-distance" capabilities from TODA Files (TODA/FP).[2] This capability allows secure asset management independently of systems verifying their validity, significantly reducing storage and operational overhead. Sato-Servers also permit seamless switching of integrity providers, enhancing adaptability without disrupting asset continuity or cryptographic lineage.
B.4 Asset Subdivision ("Spawning") and Merging
Earth64’s trie structure natively supports secure and cryptographically verifiable asset subdivision and merging operations through three distinct mechanisms:
Spawning: An asset at address P spawns two new child assets at its immediate child addresses (P0 and P1), while preserving the original parent asset at address P. This mechanism supports HyperCycle operations such as license production and Node Factory subdivision, maintaining ongoing accessibility of parent licenses for continued operation and future unlocks.
Splitting: A subclass of subdivision that creates two new assets at the child addresses (P0 and P1) and renders the original parent asset at address P inactive or inaccessible. This mechanism is particularly suitable for managing economically valuable assets such as CHyPC(e) identity collateral, where explicit parent continuity is unnecessary or undesirable.
Merging: Conversely, merging allows two sibling assets at child addresses, i.e. P0 and P1, to recombine into a single asset at their parent address P, enabling dynamic consolidation of assets when operationally or economically beneficial.
The flexibility provided by Earth64's native operations—spawning, splitting, and merging—enables HyperCycle to precisely manage its diverse licensing and collateral requirements, ensuring optimal alignment between data structures and their economic or operational roles.[4]
Note: HyperCycle's usage of the term "splitting," particularly in the context of "Node Factory splitting," refers specifically to the subdivision of a Node Factory into independently operating sub-factories. While related, this usage differs from Earth64’s narrower technical definition, which explicitly renders the parent node inactive.
B.5 Example: License Hierarchy and Unlocking in a Simplified Earth64 Tree
Licenses within HyperCycle map directly onto Earth64’s binary trie structure. The following schematic example illustrates the hierarchical unlocking and spawning pattern of licenses within HyperCycle.
Simplified License Unlocking Example:
A Node Factory License at level 10 (represented as binary address "P") reaches a Tilling Score of 2.0, allowing an unlock event to be triggered:
-
Unlocks two Network Node Licenses at level 9 ("P0" and "P1").
These level 9 Network Node Licenses ("P0" and "P1") subsequently achieve a Tilling Score of 2.0 and trigger unlock events:
-
License "P0" unlocks two level 8 Network Node Licenses ("P00" and "P01").
-
License "P1" unlocks two level 8 Network Node Licenses ("P10" and "P11").
This unlocking pattern continues recursively for each lower-level license. For instance, the level 8 Network Node License ("P01") upon achieving a Tilling Score of 2.0 would unlock two level 7 Network Node Licenses ("P010" and "P011"), and so forth, down to level 1 licenses. Level 1 Network Node Licenses can activate their corresponding nodes but cannot directly unlock further licenses.
This example demonstrates Earth64’s hierarchical addressing and systematic unlocking of Node Factory licenses, clearly highlighting its structural advantages for license management within the HyperCycle ecosystem.
B.6 Relationship between Licenses and CHyPC(e) Assets
The hierarchical structure of CHyPC(e) identity collateral mirrors precisely the hierarchy of licenses in a Node Factory that they economically back, although their positions differ within the Earth64 trie. Each CHyPC(e) token contains an amount of HyPC(e) tokens exactly equal to the total Network Node Licenses producible by the corresponding Node Factory license, ensuring verifiable economic collateral and cryptographic identity alignment.
When Node Factories undergo splitting operations, CHyPC(e) assets are partitioned carefully among parent and child licenses, reflecting the more complex collateral requirements necessary to preserve cryptographic identity backing and operational continuity, without requiring the creation of any new tokens.
Appendix C: A Comparative Analysis of Agent Communication Protocols
Protocols
This appendix provides a comparative analysis of prominent agent communication protocols emerging from the growth of large-scale AI. These protocols often target complementary layers within agent-based interactions. HyperCycle distinguishes itself primarily by providing a native, high-performance economic settlement layer, a component typically absent from other frameworks.
C.1 Overview and Comparative Matrix
The following table summarizes key differences and similarities among prominent agent communication protocols:
Table C.1: Comparative Matrix of Agent Communication Protocols

C.2 HyperCycle: Economic Settlement Layer for Agent Communication
HyperCycle’s unique value proposition lies in delivering a native, decentralized, and highly efficient economic settlement mechanism for agent interactions. Built upon the TODA/IP ledgerless consensus protocol and Earth64 hierarchical data structures, HyperCycle supports secure, rapid micropayments and computational transactions without reliance on intermediaries.[1,4]
In particular, HyperCycle uses cryptographic payment commitments and computational attestations to securely manage peer-to-peer micropayments and computational tasks. Its economic model relies on Node Factories, which deterministically produce Network Nodes based on performance measured through the Tilling process. This arrangement aligns economic incentives, rewarding sustained operational quality and supporting secure, scalable network growth.
C.3 Google A2A (Agent-to-Agent): Collaboration and Task Orchestration
Google’s Agent2Agent (A2A) is an open protocol designed to enable structured communication and collaboration among AI agents developed on diverse frameworks. A2A operates via a client-server model, where "Client Agents" initiate requests and "Remote Agents" fulfill tasks.[5] It standardizes communication around structured Tasks (stateful units of work) and Messages, enabling multi-modal agent interactions (text, files, etc.).
Key technical features include:
-
Communication using JSON-RPC 2.0 over HTTPS, combined with Server-Sent Events (SSE) for real-time streaming.
-
Agent discovery through "Agent Cards"—JSON files detailing agent identity, capabilities, and endpoints.
-
Strong support for agent-to-agent collaboration without exposing internal implementations.
While A2A standardizes agent collaboration, it does not inherently provide economic settlement capabilities. Thus, A2A’s collaborative model could be combined with HyperCycle’s secure economic settlement layer to enable comprehensive agent workflows involving both structured collaboration and financial transactions.
C.4 Anthropic MCP (Model Context Protocol): Agent-to-Tool Integration
Anthropic’s Model Context Protocol (MCP) is an open, standardized protocol for integrating AI agents with external tools, data sources, and computational resources.[6] Often described as a "USB port for AI," MCP addresses the complexity of connecting multiple AI models with diverse external capabilities.[6]
Key characteristics of MCP include:
-
JSON-RPC 2.0 over HTTPS communication, clearly defining capabilities exposed by MCP servers: Resources (data); Tools (functions); and Prompts (reusable templates).
-
A host-controlled sandbox security model, requiring user consent and managed permissions for tool execution or resource access.
-
Solves the integration challenge of linking multiple AI models to diverse external resources efficiently and securely.
MCP's integration-oriented design complements HyperCycle’s native economic settlement functionality. Used together, MCP could standardize interactions between agents and external resources,[6] while HyperCycle ensures secure, efficient economic transactions.
C.5 Microsoft NLweb (Natural Language Web): Conversational Interfaces
Microsoft’s NLweb is a specific implementation built on top of MCP, aimed at simplifying the creation of conversational interfaces for existing websites. NLweb leverages structured web data (e.g., Schema.org markup, RSS feeds) ingested into vector databases.[7] Users pose natural language queries, and an LLM performs semantic searches over ingested content to produce conversational responses.
Notable features of NLweb:
-
Built directly atop the MCP protocol standard; each NLweb instance serves as an MCP server.
-
Leverages existing web standards and structured data, lowering the barrier for website owners to enable conversational AI interactions.
-
A turnkey solution designed for a specific problem: conversational querying of web content.
NLweb, as an application-layer use-case of MCP, focuses on ease-of-implementation for conversational interactions, but does not include economic transaction capabilities.[7] Integrating NLweb applications with HyperCycle’s micropayment and settlement layer could enable monetized conversational interactions with AI agents.
C.6 Complementary Layers and Integration Possibilities
Each of these protocols addresses complementary aspects of agent-based interactions:
-
HyperCycle addresses secure, efficient economic settlement and micropayment transactions between AI agents.
-
Google A2A focuses on standardized agent-to-agent collaboration and task orchestration without built-in economic settlement.[5]
-
Anthropic MCP provides a universal standard for agent-to-tool integrations, solving complex integration challenges.[6]
-
Microsoft NLweb demonstrates MCP’s practical application for conversational interactions on websites, clearly leveraging existing web infrastructure.[7]
HyperCycle occupies a critical niche by providing secure, native economic settlement capabilities essential for comprehensive agent-based ecosystems. Integrating HyperCycle’s economic functionality with complementary protocols like A2A, MCP, and NLweb can deliver robust, flexible, and economically sustainable AI agent interactions and use-cases.
Appendix D: Architectures for an Internet of Agents:
The MIT NANDA Initiative
NANDA proposes a layered architecture comprising several distinct but interconnected layers:
Protocol Layer
This layer integrates and builds upon existing agent-to-agent communication standards such as Anthropic’s MCP (Model Context Protocol)[6] and Google’s A2A (Agent2Agent)[5]. Rather than developing yet another communication standard, NANDA aims to provide a unified communication fabric, ensuring interoperability and standardization for diverse AI agent implementations.[8]
Infrastructure Layer (Core Contribution)
NANDA’s core contributions reside within the Infrastructure Layer, providing essential services required for a decentralized ecosystem to function effectively:
-
Registry: A decentralized registry service allowing robust and efficient discovery of agents, tools, resources, and capabilities within the network. Agents can dynamically discover each other’s capabilities and endpoints without reliance on central intermediaries.[10]
-
Authentication: Secure protocols designed specifically for verifying the identity of agents and establishing trust. Robust authentication ensures that agents interact reliably in collaborative environments.[8,9]
-
Trace: A verifiable, cryptographically secured system that records interactions and exchanges among agents, ensuring accountability, transparency, and auditability within the decentralized ecosystem. Additionally, NANDA's design includes methods for confidential search, allowing agents to securely query distributed knowledge without compromising sensitive data.[8,9]
-
Search: Distributed mechanisms for querying and retrieving knowledge and capabilities across the entire agent network, facilitating seamless and efficient interaction and cooperation.[8,9]
Developer Tools & Applications Layer
This topmost layer consists of Software Development Kits (SDKs), frameworks, and third-party integration tools that allow developers to build sophisticated applications using the NANDA infrastructure. It supports rapid development, deployment, and integration of decentralized agent-based applications.[8,10]
D.3 Complementarity with HyperCycle
The NANDA framework complements HyperCycle by providing crucial infrastructure for decentralized agent discovery, authentication, and coordination, while HyperCycle specifically addresses the secure and efficient economic settlement and transactional requirements of agent interactions. These distinct capabilities allow for a highly complementary integration:
Consider a representative scenario illustrating how HyperCycle nodes communicate within an integrated NANDA-based ecosystem:
-
Discovery and Identification (NANDA Registry):
A HyperCycle Network Node, acting as an AI agent, uses NANDA’s decentralized registry services to discover and verify the identities and capabilities of other Network Nodes in the network, enabling dynamic and secure matching of agents for tasks.
-
Collaboration and Coordination (Google A2A):
The nodes leverage standardized agent communication protocols such as Google's A2A for structured task orchestration. HyperCycle nodes exchange task instructions and negotiate workflows securely and efficiently, coordinating execution steps clearly defined through A2A standards.
-
External Tool Integration (Anthropic MCP):
HyperCycle Network Nodes utilize Anthropic's MCP standard to interact securely with external tools and data resources. MCP provides a standardized interface for HyperCycle nodes to extend their capabilities and securely access specialized external services and computational resources as required.
-
Economic Settlement (HyperCycle's Economic Layer via TODA/IP):
HyperCycle Network Nodes settle micropayments and computational transactions rapidly and securely through HyperCycle’s own economic settlement layer, built on the ledgerless TODA/IP protocol. After securely coordinating and executing tasks, nodes finalize payments explicitly and independently, ensuring efficient economic exchanges without intermediaries.
Together, the NANDA framework and HyperCycle’s Network Nodes form a cohesive, secure, and efficient architecture for global AI-agent collaboration. This combined approach effectively supports decentralized agent discovery, secure task coordination, flexible integration with external tools, and secure, high-performance economic settlement—enabling robust decentralized collaboration at scale. Crucially, this example illustrates how HyperCycle naturally accommodates complementary protocols, yet the flexibility of its architecture also allows it to adapt readily to alternative or replacement protocols as the IoAI ecosystem continues to evolve.
Appendix E: Governance and Alignment in Agentic Systems
This appendix discusses the critical importance of safety, governance, and ethical alignment within decentralized AI ecosystems. While HyperCycle facilitates secure economic settlement and computational interactions, ensuring these interactions remain aligned with human values is essential for the long-term viability and acceptability of a global Internet of AI.
E.1 The Importance of Ethical Alignment and Governance
As AI agents grow increasingly autonomous and economically active, strong governance and alignment measures become essential. Alignment—ensuring agent behavior remains safe, trustworthy, and beneficial—is a critical factor in enabling sustainable growth of decentralized AI ecosystems.
E.2 Illustrative Example: Anthropic’s Constitutional AI
One notable example highlighting contemporary thinking on alignment is Anthropic’s Constitutional AI.11 This approach involves training AI models to adhere to ethical guidelines defined in a human-written "constitution."
Key features of Constitutional AI include:
-
Clear ethical principles promoting honesty, helpfulness, harm avoidance, and respectful interactions.
-
A two-phase training approach, Reinforcement Learning from AI Feedback (RLAIF), enabling models to critique and iteratively refine responses according to constitutional principles, thus minimizing the need for extensive human oversight.
Anthropic's Constitutional AI demonstrates how ethical considerations can be systematically embedded within AI models, offering a prominent example of current alignment methodologies.
E.3 Complementary Alignment Opportunities through Market-Based Reputation Mechanisms
While HyperCycle's core reputation system, embedded within the Tilling mechanism, measures operational metrics like uptime, computational accuracy, and transaction reliability, there exists a complementary opportunity to leverage HyperCycle’s underlying cryptographic proof system to support marketplace-driven alignment and governance measures.
Specifically, independent marketplace operators and ecosystem participants could build additional reputation mechanisms using HyperCycle’s existing cryptographic proof infrastructure. These marketplace-specific reputation measures could, in principle, incorporate alignment-focused metrics or criteria tailored to specific AI applications or submarkets. For example, marketplaces particularly concerned with alignment or safety could introduce reputation incentives that reward nodes demonstrating behavior aligned with explicit ethical principles or safety standards.
This approach naturally leverages the flexibility of HyperCycle’s proof infrastructure, allowing different marketplaces to adapt reputational incentives and measures according to evolving alignment needs. While these alignment-focused reputation systems represent a promising direction for further exploration, their exact form and implementation would emerge as the market matures and as the ecosystem identifies explicit opportunities to integrate alignment-oriented incentives into node selection protocols or methods.
E.4 Alignment as a Collaborative, Evolving Effort
Ensuring robust alignment and governance is an ongoing, collaborative challenge. HyperCycle maintains a clear commitment to adaptively engage and collaborate with diverse stakeholders, including academic initiatives (such as MIT's NANDA),[8] industry leaders (such as Anthropic's Constitutional AI),[11] and open-source or community-driven initiatives.
Through these collaborative relationships, HyperCycle aims to continuously refine its approaches to governance and alignment, supporting the safe, effective, and responsible evolution of decentralized AI systems within a truly global and open Internet of AI.
Appendix F: Glossary of Terms
-
Advanced Node Factory Enclosure (ANFE): An ERC-721 token representation of a Node Factory, primarily on the Base blockchain. It serves as a public registry pointer to the native Earth64 Sato-Server asset, designed for portability and composability with third-party software licenses.
-
AI Machine (AIM): A modular, containerized (e.g., Docker) execution environment within a HyperCycle Node. It performs computational workloads as dispatched by the Virtual Machine (VM).
-
Boundary Node (HBN): A HyperCycle Boundary Node. A HyperCycle node activated by a level 10 Node Factory License. Provides hybrid services utilizing computational resources from the IoAI, monetized externally. May convert to a Network Node upon meeting predefined economic performance criteria.
-
CHyPC(e): A non-fungible cryptographic asset, represented as an ERC-721 pointer, that serves as the exclusive identity-backing collateral for a Node Factory. Its economic value in the underlying HyPC(e) token is algorithmically tied to the total number of Network Nodes the factory can produce.
-
Earth64: A hierarchical data structure, addressed using a binary trie of fixed depth, that provides a globally unique, deterministic address space for digital assets. It supports native asset containerization, subdivision, and merging.
-
HyPC(e): The underlying fungible token (e.g., ERC-20) that provides the economic value for CHyPC and CHyPCe identity tokens.
-
Merkle Module: A component on each node that generates local Merkle proofs of the node's operational metrics (uptime, computation, reputation) for each network cycle.
-
Merklizer Service: A network service that aggregates local Merkle proofs from all nodes into a single, global Merkle root hash (a block) periodically, cementing the network's state for that cycle.
-
Network Node (HNN): A HyperCycle Network Node. A full-stack instance of the HyperCycle Node Software (HNS) activated by a Network Node License. It is capable of directly providing and consuming computational services via P2P transactions.
-
Network Node License: Licenses (levels 9–1) able to activate Network Nodes, enabling direct participation in IoAI peer-to-peer computational markets and can trigger subsequent license unlocks (except at level 1).
-
Node Factory: A digital asset, natively an Earth64 Sato-Server, comprising a hierarchical collection of licenses paired with a CHyPC token. It is the generative source of all licenses within the HyperCycle ecosystem.
-
Node Factory Bundle License: Licenses (levels 19–11) representing bundles of Node Factories. Primarily economic and structural but may optionally perform uptime-based tilling.
-
Node Factory License: Level 10 license initially able to activate a Boundary Node; enables unlocking of the first Network Node Licenses (at level 9) in a Node Factory.
-
Node Manager (NM): The administrative and message-routing component of a HyperCycle Node, coordinating internal components and managing configuration.
-
Sato-Server: A cryptographically secured, transmissible container associated with a unique address in the Earth64 data structure. It can hold any digital asset, with its integrity managed independently of its state via TODA/FP.
-
Tilling: The continuous Proof-of-Performance mechanism in HyperCycle. It cryptographically records and validates a node's operational metrics to calculate a Tilling Score.
-
Tilling Score: A composite numerical score (S) calculated from a node's uptime, computation, and reputation ratios. It governs the unlocking of new licenses and serves as a measure of cumulative performance and reliability for a license before and after an unlock event. Licenses start at 1.0 and accumulate scores continuously; reaching 2.0 allows explicit unlocking events.
-
Transaction Finality: The state at which a transaction is irreversible. HyperCycle asserts a two-tier model: near-instant local finality for cryptographic commitments and global economic finality (re-spendability) upon the publication of a global block every 6-30 seconds.
-
Transaction Machine (TM): The economic settlement component of a Network Node, responsible for managing secure micropayments using ledgerless protocols such as TODA/IP.
-
TODA/FP (File Protocol): A cryptographic data structure and associated protocols, where the data structure separates an asset's state from its integrity (non-equivocation), enabling "integrity-at-a-distance".
-
TODA/IP (Internet Protocol): A ledgerless, P2P communication protocol for value transfer, asserted to operate at the network packet level and use a Deterministic Distributed Computing consensus mechanism.
-
Virtual Machine (VM): The central logic orchestrator within a HyperCycle Node, responsible for executing programmable workflows and coordinating all other components.
References
References are numbered based on their relevance and importance to our technology, followed by complementary technologies, background references, and finally informal sources, rather than by their order of appearance in the text.
-
Saliba T, Toliver D. TODA/IP Protocol V2.3 An Internet Communication Protocol. 2019.
Available from: https://assets-global.website-files.com/65bca354e4d63fa96d96a764/65e0b18356d42a7973507a35_65d71ef8a2791856c8927db2_TodaIP_ProtocolV2.3.pdf [URL valid as of 2025 Jul 10]
-
Coward K, Toliver DR. Simple Rigs Hold Fast. T.R.I.E.
Available from: https://trie.site/simple_rigs_hold_fast.pdf [URL valid as of 2025 Jul 10]
-
Coward K, Toliver DR, Sulpizi C, Gravitis A, Fertman A, Moir R, et al. Rigging Specifications v0.9876. T.R.I.E.; 2023. Available from: https://trie.site/rigging_specifications.pdf [URL valid as of 2025 Jul 10]
-
Saliba T, Moir R, Toliver D, Rowe BR, Radley J, Tran B. Earth64 Data Structure V1.0.2. 2022.
Available from: https://www.earth64.com/_files/ugd/54374c_19625276cf6b41dd8b0954c9f298b802.pdf [URL valid as of 2025 Jul 10]
-
Agent2Agent Protocol. The A2A Project. Google; 2024.
Available from: https://a2aproject.github.io/A2A/latest/ [accessed 2025 Jul 10]
-
Anthropic. Model Context Protocol (MCP): Introduction. 2024.
Available from: https://modelcontextprotocol.io/introduction [accessed 2025 Jul 10]
-
Microsoft. Introducing NLWeb: Bringing conversational interfaces directly to the web. Microsoft Source; 2024 May 20.
Available from: https://news.microsoft.com/source/features/company-news/introducing-nlweb-bringing-conversational-interfaces-directly-to-the-web/ [accessed 2025 Jul 10]
-
MIT Media Lab. NANDA: The Internet of AI Agents. 2025.
Available from: https://nanda.media.mit.edu/ [accessed 2025 Jul 10]
-
MIT Media Lab. NANDA: The Internet of AI Agents Perspective Paper. 2024.
Available from: https://nanda.media.mit.edu/decentralized_AI_perspective.pdf [URL valid as of 2025 Jul 10]
-
MIT Media Lab. Hub for Decentralized Agent Communication. 2025.
Available from: https://ui.nanda-registry.com/ [accessed 2025 Jul 10]
-
Bai Y, Kadavath S, Kundu S, Askell A, Kernion J, Jones A, et al. Constitutional AI: Harmlessness from AI Feedback, arXiv preprint (v1: 2022 Dec 15).
Available from: https://arxiv.org/pdf/2212.08073 [URL valid as of 2025 Jul 10]
-
Nakamoto S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008 Oct 31.
Available from: https://bitcoin.org/bitcoin.pdf [URL valid as of 2025 Jul 10]
-
Back A. Hashcash: A Denial of Service Counter-Measure. 2002 Aug 1.
Available from: http://www.hashcash.org/papers/hashcash.pdf [URL valid as of 2025 Jul 10]
-
Gencer AE, Basu S, Eyal I, van Renesse R, Sirer EG. Decentralization in Bitcoin and Ethereum Networks, arXiv preprint (v1: 2018 Jan 11).
Available from: https://arxiv.org/pdf/1801.03998 [URL valid as of 2025 Jul 10]
-
Marcus A. How AI Protocols Will Expand Enterprise Boundaries. Salesforce Blog; 2023 Jul 31.
Available from: https://www.salesforce.com/blog/how-ai-protocols-will-expand-enterprise-boundaries [accessed 2025 Jul 10]
